The nature of our platform, being one that proactively monitors, puts DomainGuard in a position where we are regularly the first security vendor to identify known and novel threats in the wild. Our threat detection logic uses a combination of automated statistical analysis combined with manual, human analyst interpretations.
DomainGuard captures metadata around the threats we identify and provides API access to allow our customers to integrate with our domain threat feed, Malist. Malist’s domain data feed allows your organization to enhance your existing security solutions and supercharge detection capabilities. As a security provider, our goal is to provide the best security possible for our customers, and one method to accomplish this goal is through integrating our threat feed, Malist, with our customers existing solutions.
Malist
Malist is DomainGuard’s threat feed which provides threat intel to our customers in a manner easily ingested by other security vendors. By being a DomainGuard customer, you receive exclusive access to threats identified in Malist, the majority of which were identified primarily by DomainGuard. Below we’ve outlined a number of important use cases for our domain data that can be used to enhance the overall security of your organization.
Malist Threat Feed Use Cases
Email Monitoring
E-mail monitoring solutions are necessary in helping organizations be better protected against phishing. These solutions, however, are limited to protecting your employees at the e-mail layer. They will not protect your brand from being abused and prevent threat actors from cloning your website, or targeting your customers. By integrating your existing email monitoring solution with Malist, you empower your solution to block lookalike or suspicious domains you otherwise would be unaware of.
DomainGuard monitors all suspicious domains relevant to your organization, and through Malist, this list of domains can be ingested into your email monitoring solution. This empowers your organization to block any email from a suspicious domain from ever reaching your users.
In addition to domain data, we track IP addresses associated with malicious activity, allowing your organization to block these IPs from also sending e-mails to your users.
Account Compromise Detection
Phishing websites regularly redirect users to the legitimate website after the threat actors have tricked users into entering credentials. This method helps divert suspicion away from the phishing website. In instances where attackers clone your website, and your organization is gathering web server logs from the redirected website you own, Malist can be used to identify potential customer account compromise.
The HTTP protocol makes use of a “Referrer” header which is the last web address loaded prior to visiting your website. As attackers redirect individuals to your webpages, we can utilize your web server logs to identify illegitimate Referrers, and potentially compromised customer accounts. I.e. customers that were redirected to one of your organizations web applications through a phishing campaign.
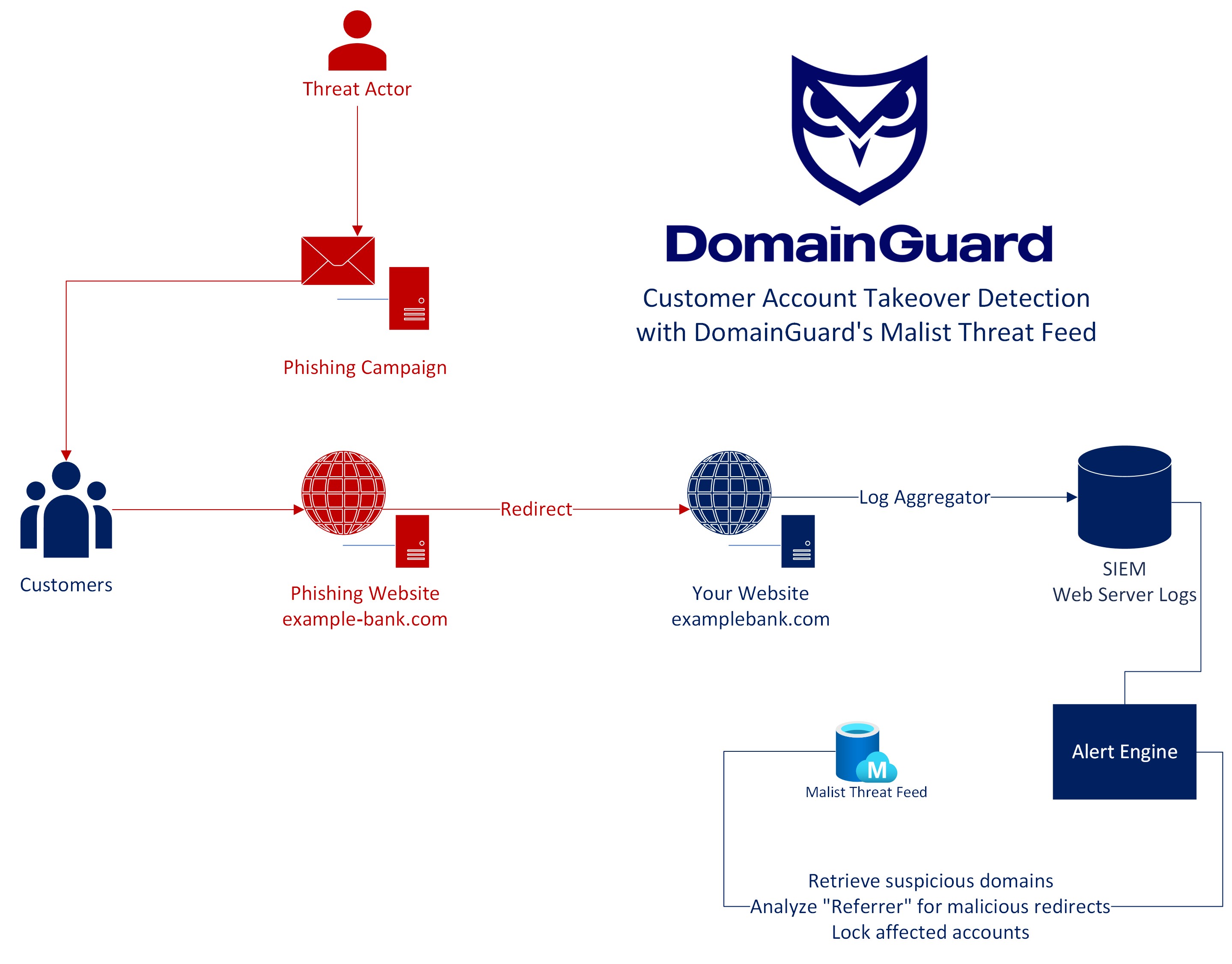
Detect Customer Account Compromises with Malist
DNS and URL Filtering
Malist integrates beautifully with DNS and URL filters which allow your organization to block domains by their Fully Qualified Domain Name (FQDN). Through automated integration with Malist, the moment DomainGuard identifies malicious activity for a domain, your existing solutions will also be made aware of the malicious domain. This allows your organization to build on it’s defense-in-depth or layered defense strategy.
By having intel on malicious or suspicious domains synchronized and integrated with your existing solutions, even if there is a delay with the domain takedown process, you’ll have the layers of defense in place to prevent your users from communicating with the malicious domains.