Phishing continues to be the easiest way into an organization and was involved in 36% of all breaches in 2020, up 11% from the year prior and likely to increase for 2021. Per discussions with local security firms:
Penetration tests where a sophisticated phishing attack is included as part of the engagement, success rates are nearly 100%.
Meaning when penetration testers are using phishing as part of the engagement, they’re going to get in. If a breach is most likely to occur through phishing, doesn’t it make sense to allocate resources to protect against phishing. DomainGuard even goes on the offensive to phight phishing - see what we did there?
How DomainGuard Phights Phishing
DomainGuard uses a combination of automated and manual analysis to regularly monitor domains and keywords associated with your brand. DomainGuard categorizes domains as suspicious when we believe the domains have a potential to negatively impact your business whether it be through phishing, impersonating your brand, or commiting fraud against your customers. The identified suspicious domains are continuously monitored by DomainGuard.
Domain Lifecycle
What makes a domain suspicious comes down to intent. Registering a look-alike domain is not malicious in and of itself, in fact, many people and organizations engage in domain-squatting as a method of generating passive income. DomainGuard continuously monitors all domains relevant to your company, brand, and we takedown the site as soon as we identify and document malicious intent.
Detect Phishing Sites during Development
Our change tracking technology has allowed us to detect several phishing websites as they were being developed. We were able to issue takedown requests while the threat actors were actively trying to build out their phishing sites. Preventing the malicious actors from ever using the phishing site against your organization.
Here we see a threat actor testing out their web page with the domain: secure01c-chasebanking.com. Safe to say the
malicious actor didn’t get past Hello World!
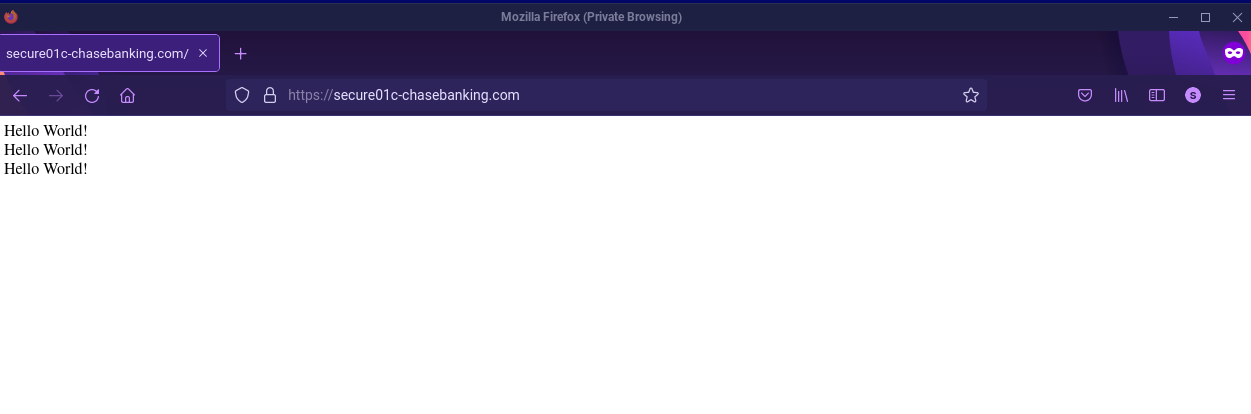
Phishing Site in Development
In this next example, we show a screenshot of a phishing site that contained an administrative login for the threat actor.
DomainGuard believes the threat actor purchased this website as a phishing kit. Phishing kits are pre-built software
suites which are sold on the darkweb and facilitate the phishing website development process.
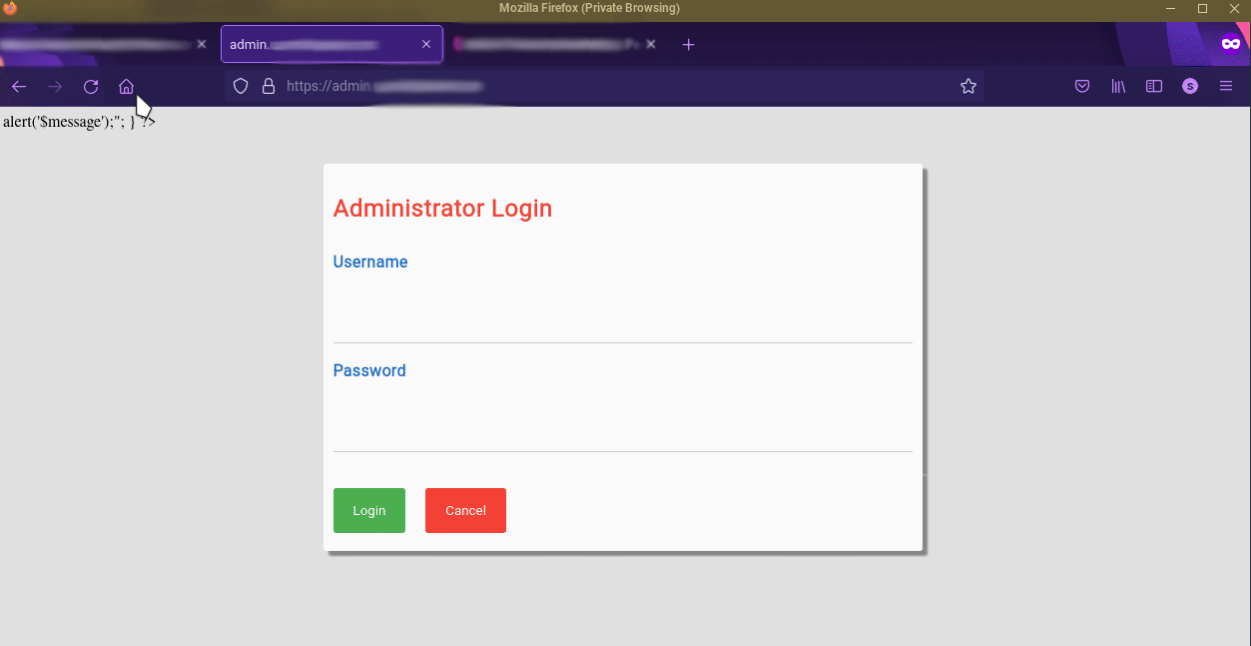
Phishing Kit Admin Login
Monitoring Works
In both the of these examples, DomainGuard was able to identify, report, document, and takedown the phishing websites listed above - rendering the phishing site useless. This is what we mean by Proactive Phishing Protection. We’re able to proactively monitor and takedown phishing sites before they even pose a threat to your organization.