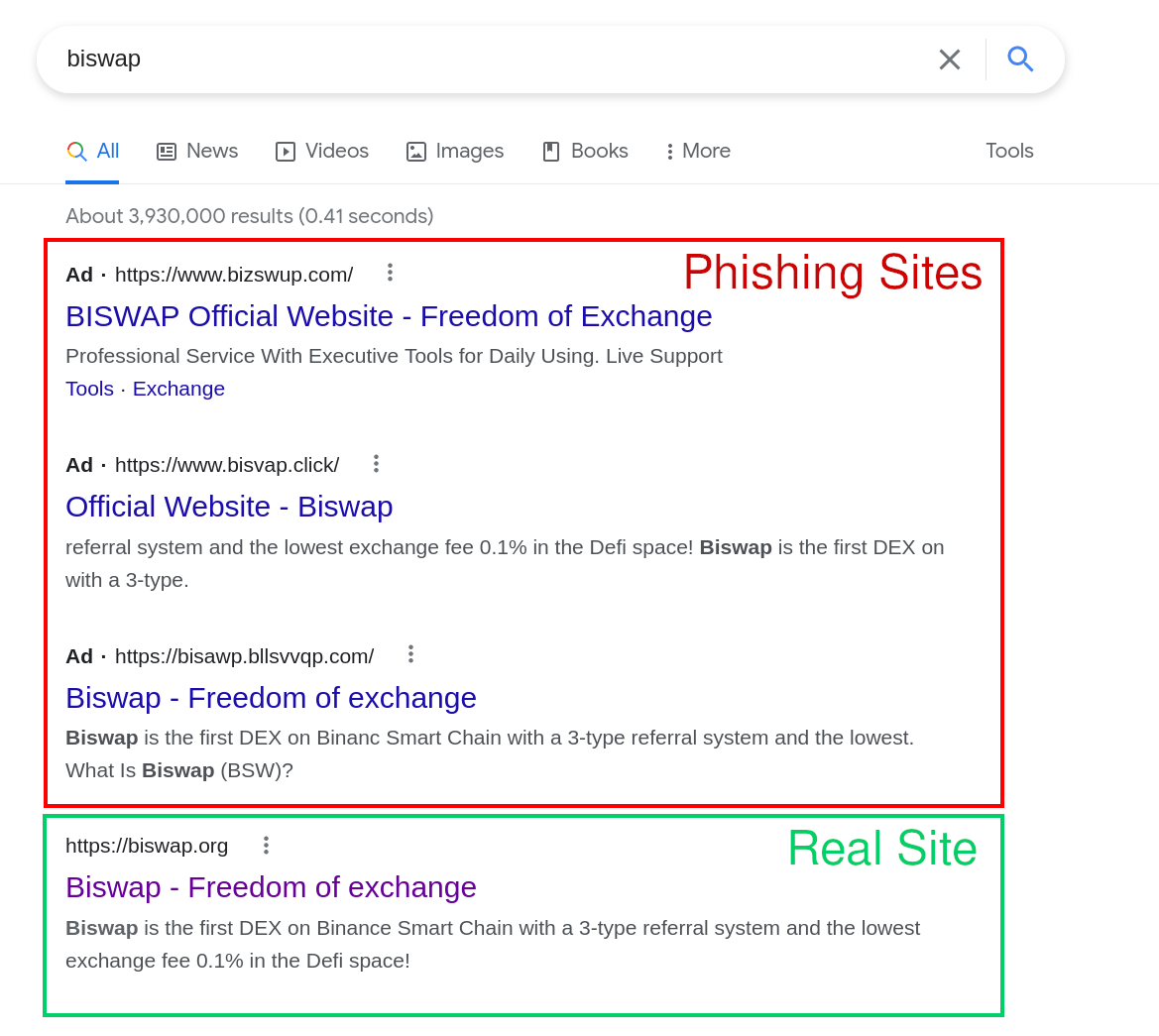
Three fake phishing sites displayed by Google Ads before the legitimate site.
Overview
When you’re trying to reach a specific website but can’t quite recall the exact URL or domain, or perhaps for sheer convenience, how often do you find yourself typing the company’s name into Google and instinctively clicking on the first link that appears?
What happens if the first link you see – and click on – is actually a phishing clone of the legitimate site you’re trying to access? The aim of this blog post is to raise awareness about how threat actors are using the Google Ads platform as a delivery mechanism for their phishing sites. Most concerning of all, threat actors have been exploiting Google Ads, formerly known as AdWords, as a phishing delivery mechanism for over a decade.
More Examples
The example we provided above is an egregious case of three phishing sites that were displayed before the actual site. All three of the domains clearly impersonated biswap.org, a crypto exchange platform. In fact, crypto-related web applications have become significant targets for this type of attack, given the ease with which a user’s wallet funds can be accessed if the attack is successful.
Below are more examples identified by @realScamSniffer on Twitter.
1/ 🚨 A recent surge in phishing scams via Google search ads has led to users losing approximately $4 million.
— Scam Sniffer | Web3 Anti-Scam (@realScamSniffer) April 27, 2023
ScamSniffer has investigated multiple cases where users clicked on malicious ads and were directed to fraudulent websites.#PhishingScams #GoogleAds pic.twitter.com/vuKCgSuFnV
In the example below, we see a report of a Google Ad being used to deliver a look-alike phishing domain for a popular e-mail client, Thunderbird.
IcedID #malvertising tricking users searching for Thunderbird on Google Search ⚠️🚨
— abuse.ch (@abuse_ch) January 30, 2023
IcedID payload hosted on Cloud Storage for Firebase:
🌐 https://t.co/LrKGsYA45Y
IcedID payload:
🪲 https://t.co/1p3VnHkJOk
IcedID C2:
🔥 https://t.co/Bl6xS4cnNK
/cc @GoogleAds pic.twitter.com/6o0TQ3HmSI
How long has this been a problem?
Well, that’s a very good question. We did some digging to find the oldest account of a malicious Google ad and while this isn’t the oldest
malicious ad we found (2008), it’s the one we wanted to share because of the irony that the target of the ad was Google themselves.
The source for the image you see below is Search Engine Land,
a very fitting name for all things search engine.
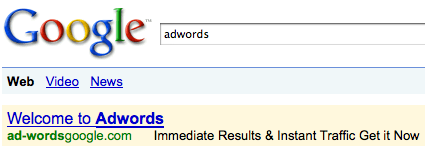
Google AdWords Phish in 2008
What you see in this image, is a Google AdWords ad, for a malicious site registered by a threat actor who then ran the Ad through the adwords platform, targeting the platform itself. As users typed “adwords” into Google, the very first link they saw was actually a phishing site delivering a malware payload. So this was in 2008, surely this type of thing doesn’t exist with all the advancements in AI and technology as a whole, right? Wrong, threat actors are still using Google Ads as a delivery mechanism for their phishing sites, and just this week DomainGuard was reporting malicious ads to Google. The domain used in 2008, available to register for anyone that would like to hold onto it for nostalgia.
ad-wordsgoogle.com
Why it works
As highlighted in our overview, and as is common with numerous other attack vectors, attackers cunningly exploit our habit of typing a keyword into a search engine and relying on the first result. Capitalizing on this convenience, attackers strategically place their phishing sites at the top of the results by running ad campaigns. Further reinforcing this tactic, attackers bank on users’ implicit trust in Google’s top results. After all, wouldn’t you assume that these top-ranking results must be reputable to earn such a coveted position?
Unfortunately, we’ve seen scenarios where the top result was a newly registered domain hosting a phishing site, with the legitimate company’s ad displayed right below the phishing ad.
Recommendations
- For end users
- Don’t click on any Google Ad until Google can get a better handle on this problem. Sorry Google - you’ve known about this for quite some time.
- For tech workers
- If you feel your company is at risk, implement monitoring for look-alike domain detection, as well as keyword monitoring for ad campaigns.
- For Google
- Prioritize getting a handle on this problem because your reputation is at risk.
Need more assistance?
If you found the information above difficult to consume or need additional assistance, please reach us by email at [email protected] or by filling out the contact form below.