Fake OpenSea "Wallet Connect" Site
tl;dr
Scammers are impersonating NFT Marketplaces on Twitter and posing as the legitimate support Twitter account for these marketplaces, notably OpenSea. The scammers reply to individuals who need help and tell them to message the fake support account for assistance directly. In the DMs, is where the nefarious activity goes down. The scammers instruct users to navigate to a fraudulent site which is a replica of the legitimate site. Users are told that in order to resolve their support inquiry, they need to “connect” or “sync” their wallet and are sent a link to the fraudulent site. Unbeknownst to the user, the process of “syncing” their wallet requires entering sensitive information on the fraudulent site.
Background
The best stories to report on are the ones that matter most in the present. At the same time you’re reading this post, fraudsters are hammering away at NFT marketplaces, creating fraudulent sites, and attempting to steal users’ crypto wallet recovery phrases. Two artists have reached out to DomainGuard specifically to inform us of how scammers used fraudulent sites to obtain the artist’s crypto wallets. This blog post will cover the current NFT marketplace support scam and display the evidence we’ve documented. In addition, we’ll show how DomainGuard can detect scam sites such as the ones mentioned and significantly reduce fraudulent site efficacy in scamming users.
NFTs 101
Before we dive into this blog post, we want to give you a quick background on NFTs. Non-fungible Tokens (NFTs) are unique identifiers that can be attached to digital assets, such as art in the form of images. These identifiers are not only unique, but they’re also immutable, meaning the token cannot change. Ownership of the token is tracked for eternity in a ledger called the blockchain. Through this blockchain technology, individuals can purchase digital assets and prove ownership and scarcity of a given asset. At this point in time, OpenSea is the largest and most widely used NFT marketplace. NFTs are becoming increasingly popular and are all over the media. Some recent NFTs have sold on the order of millions of dollars and are one of the several reasons NFT marketplaces are becoming a juicy target for scammers.
The Scam
Fake Support Accounts
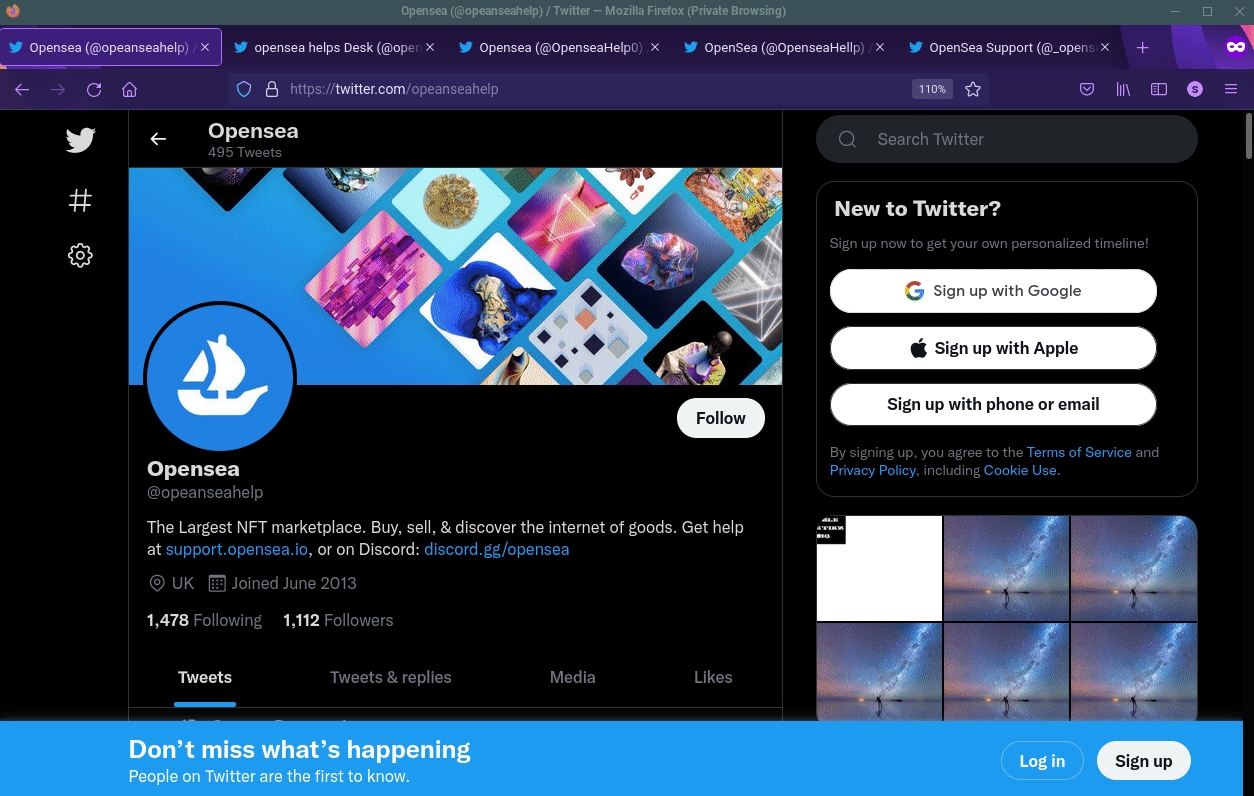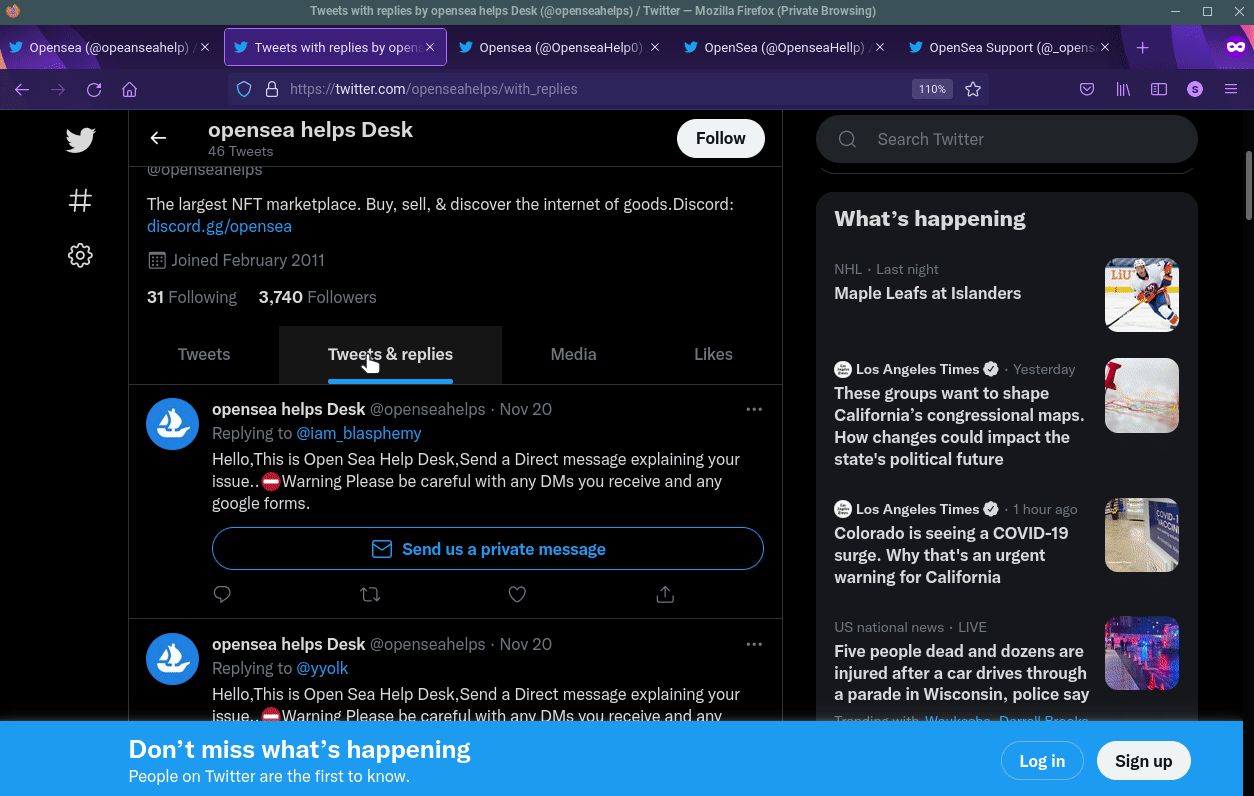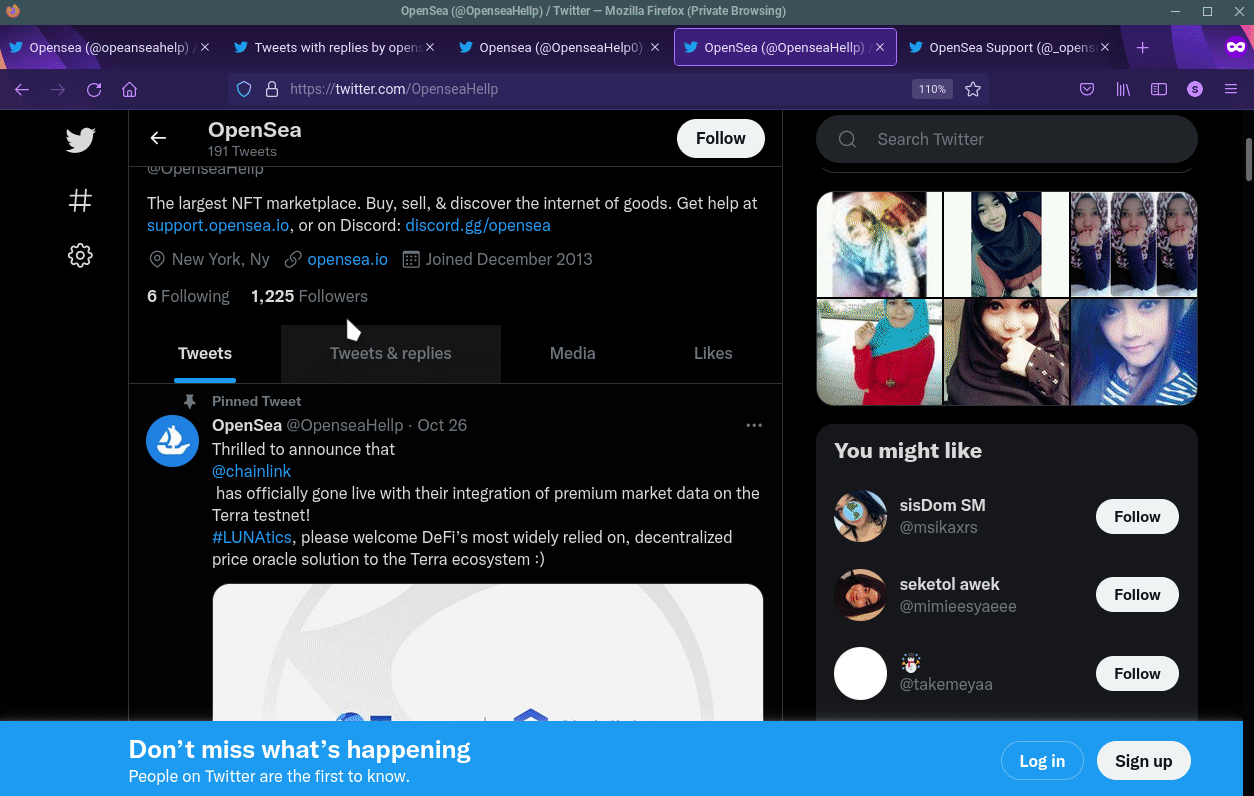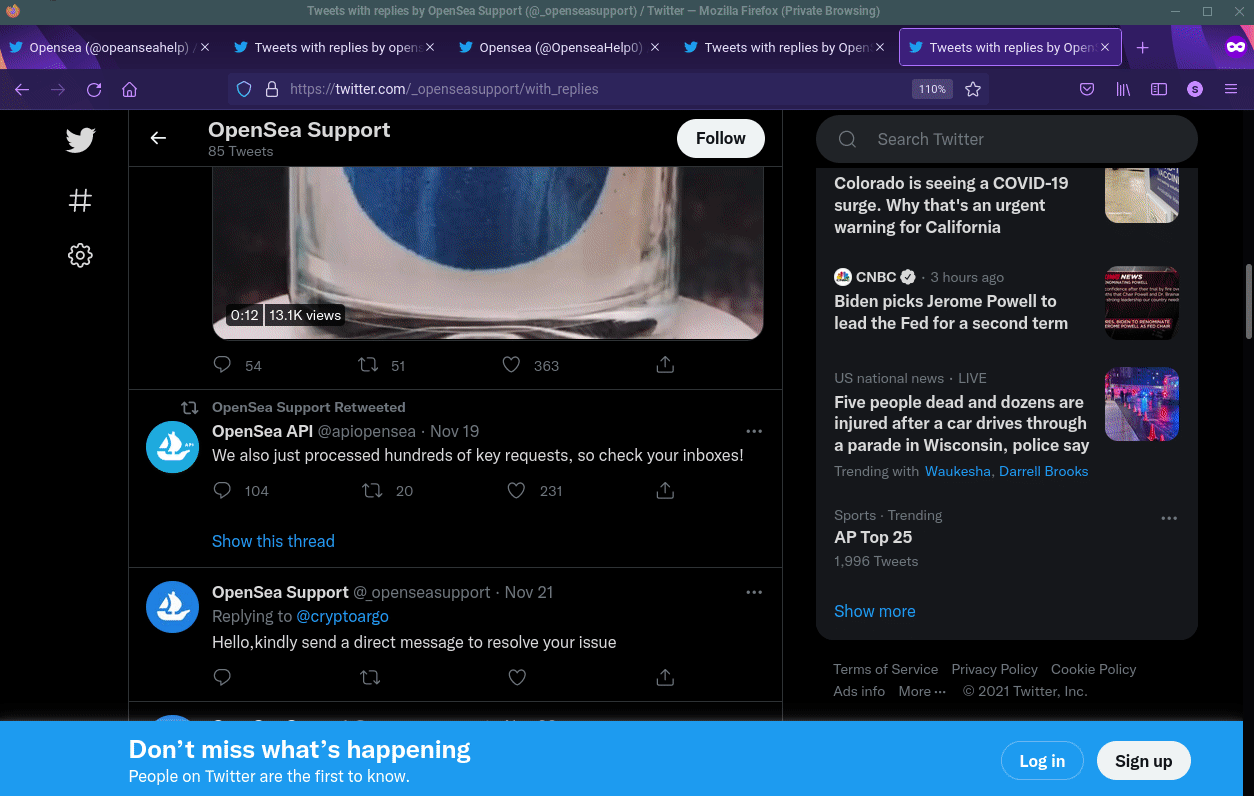
Many users are taking to Twitter as they’ve reported an increased delay in the time it takes them to receive a reply on their OpenSea support inquiry. Unfortunately, scammers are taking advantage of this delay and replying directly to users’ tweets, jumping at the bit to provide quick “customer service”. The users have a reason to interact with the account as they are hoping “OpenSea Twitter Support” may resolve their issue much quicker. People resort to Twitter when needing assistance and as such, it is not unusual for individuals to tweet @OpenSea or any company for support. Scammers step in with their illegitimate accounts and try to trick users into thinking they are the real OpenSea support Twitter account.
Below we show a user who is tweeting @opensea to receive an update on their ticket status. The fake support account quickly jumps on this opportunity to “help” the user.
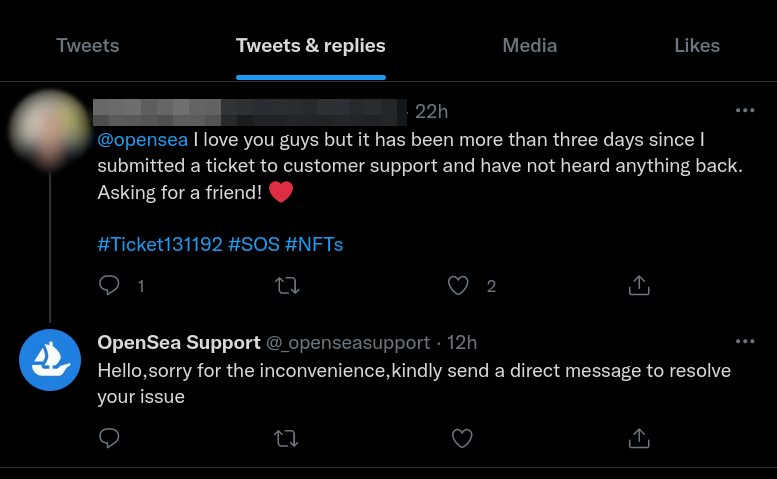
User tweeting for support and received reply from a fake account.
Not only did the fake account @_openseasupport reply to the user, but they also had one of their cohorts reply to the user and inform them
to reach out to the fake support account, and that they would be able to assist. Cleopatra is a scammer or is helping the scammers.
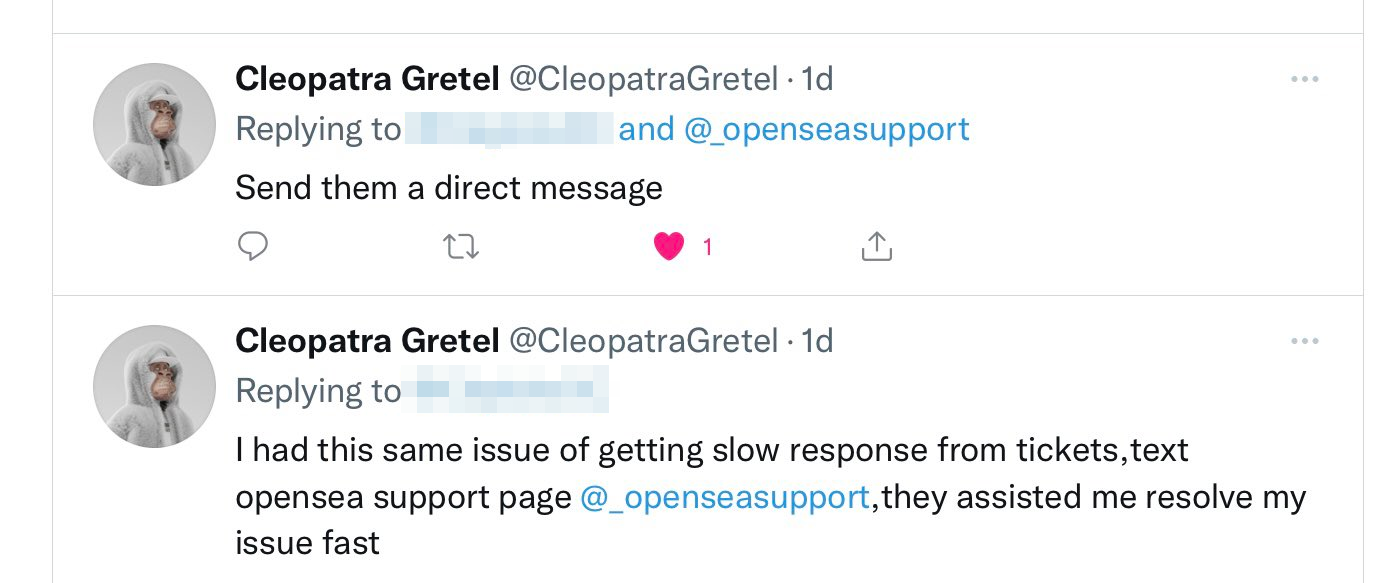
Scammer vouching for the support account.
What actually goes down in the DMs
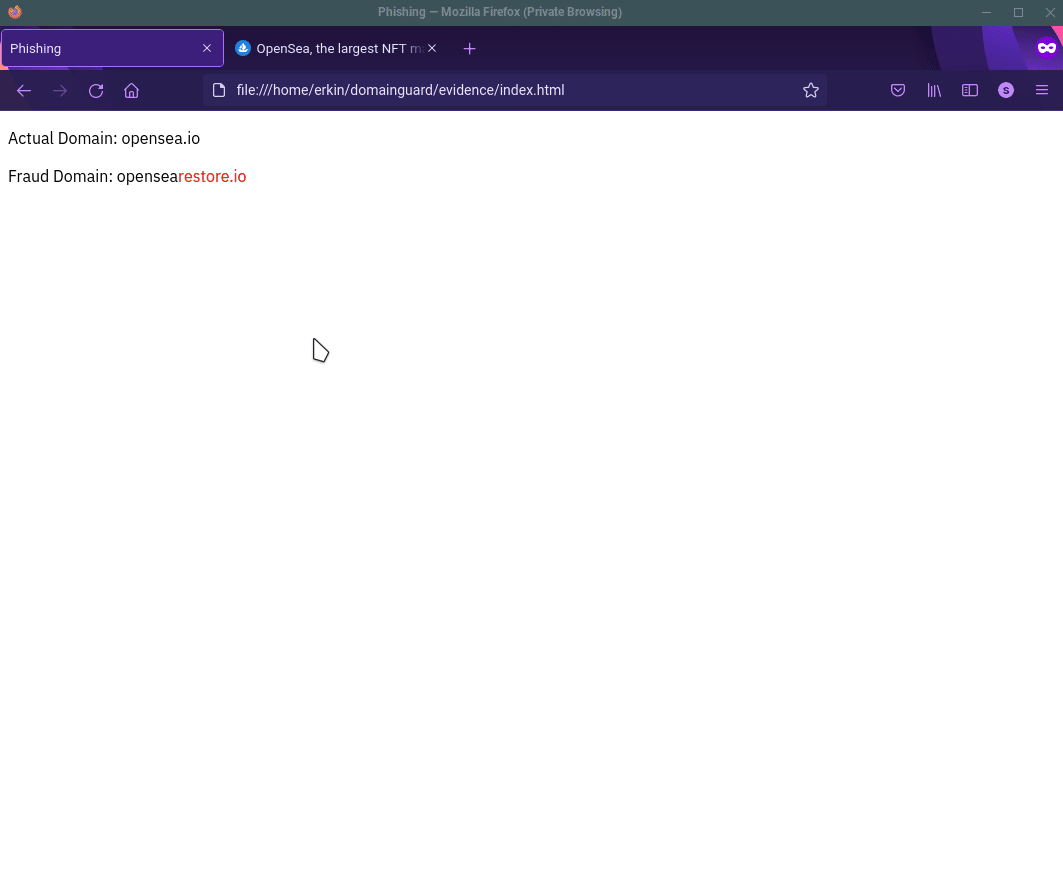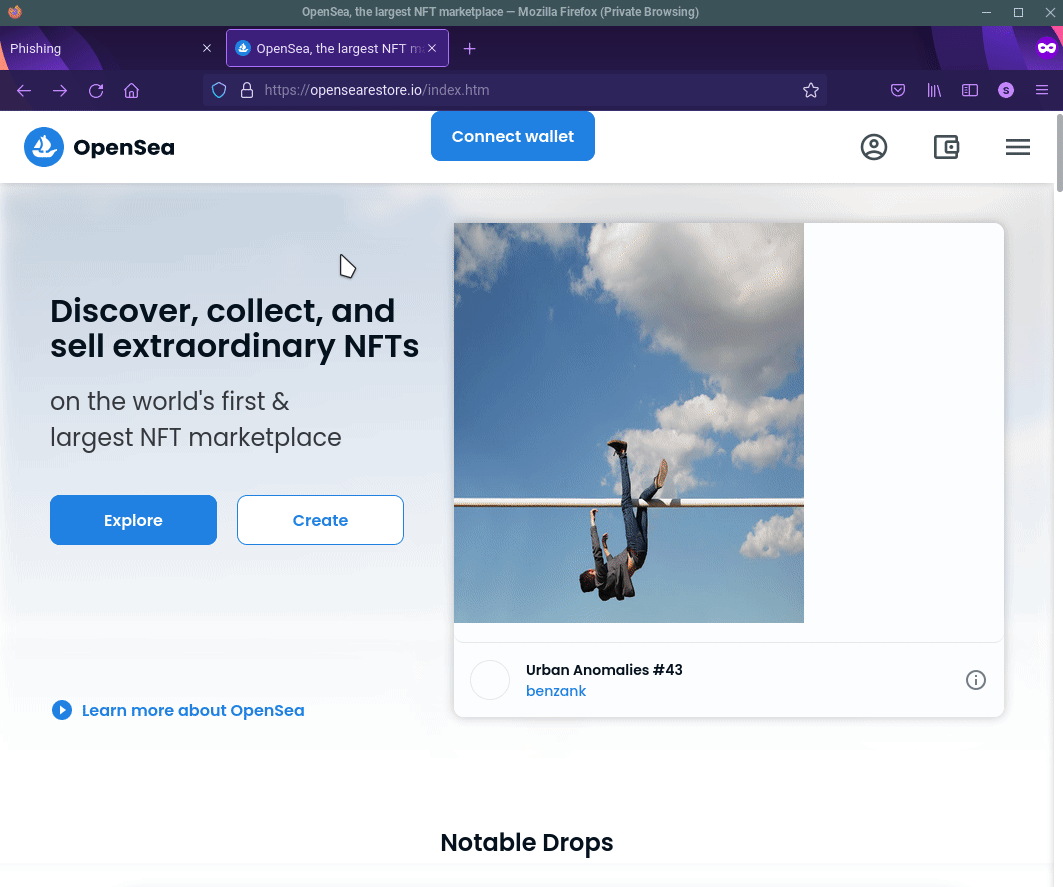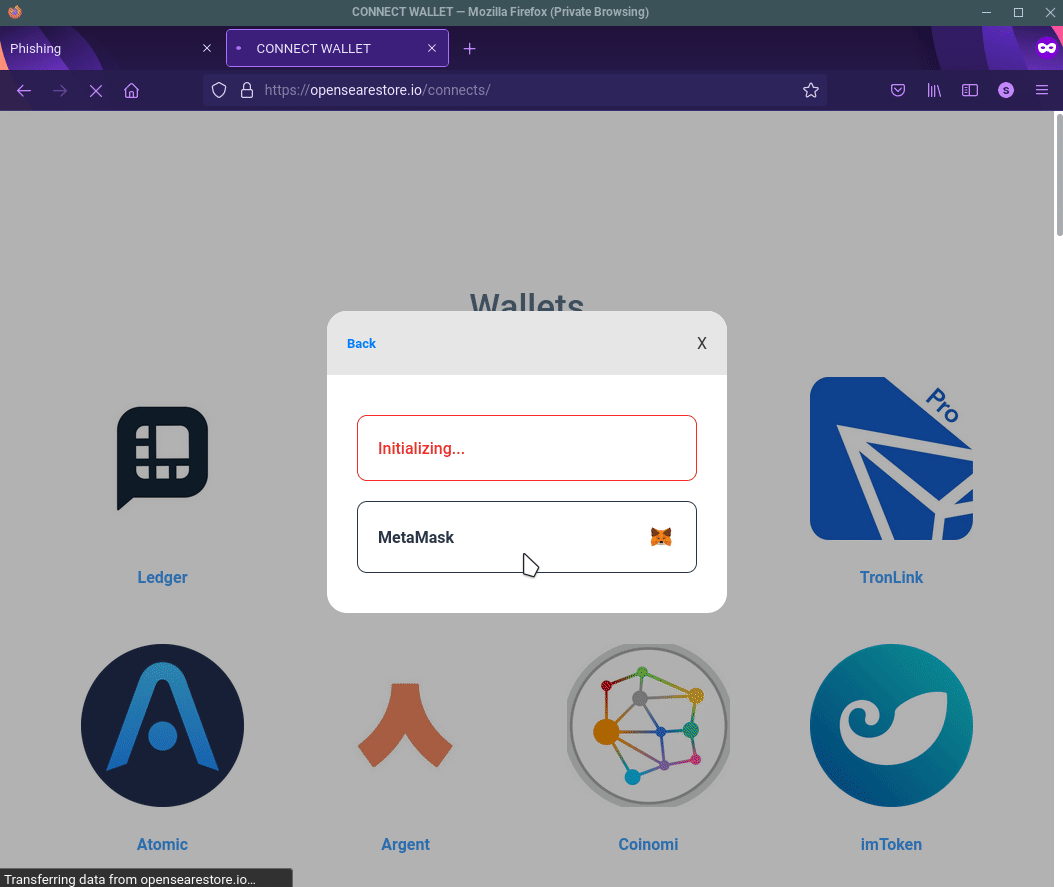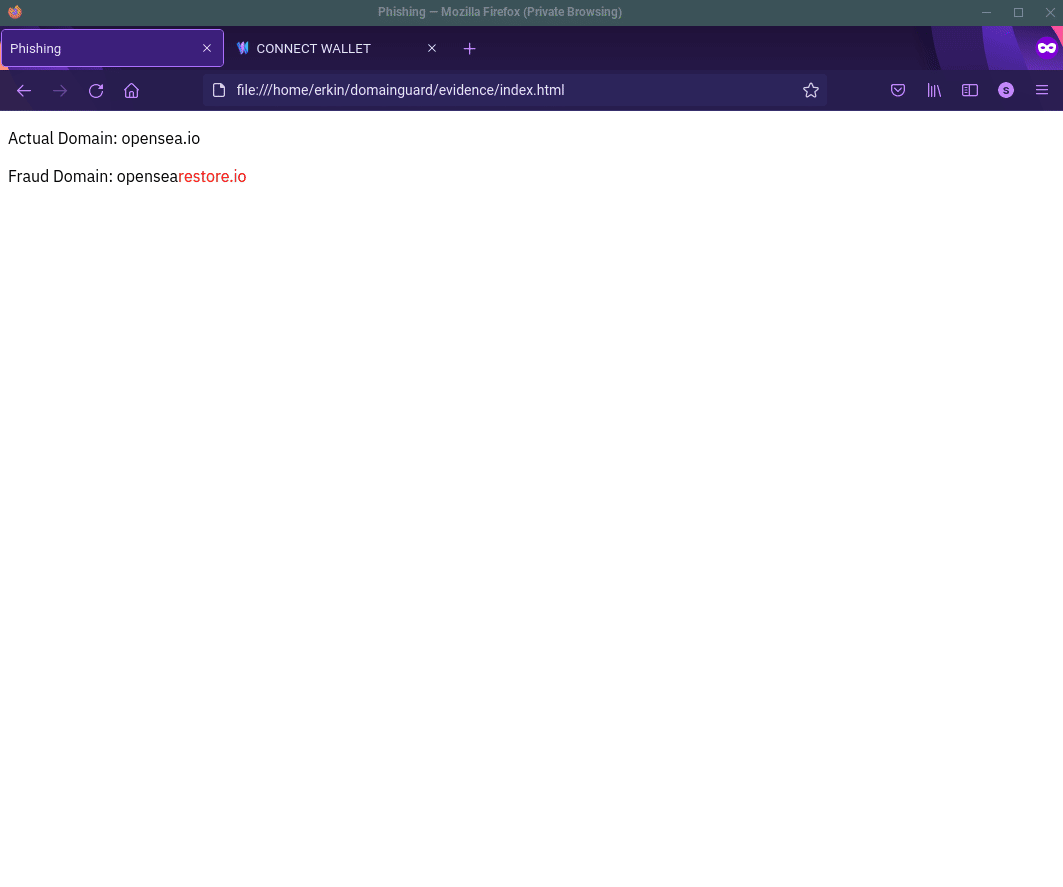
When the users direct message the fake support account, below is an example of the interaction you would expect to see. As you can see, the scammers instruct users to “restore” or “connect” their wallet and provide a link to a website that is a malicious clone of OpenSea’s legitimate website. DomainGuard detected and reported on the domain in question: opensearestore.io
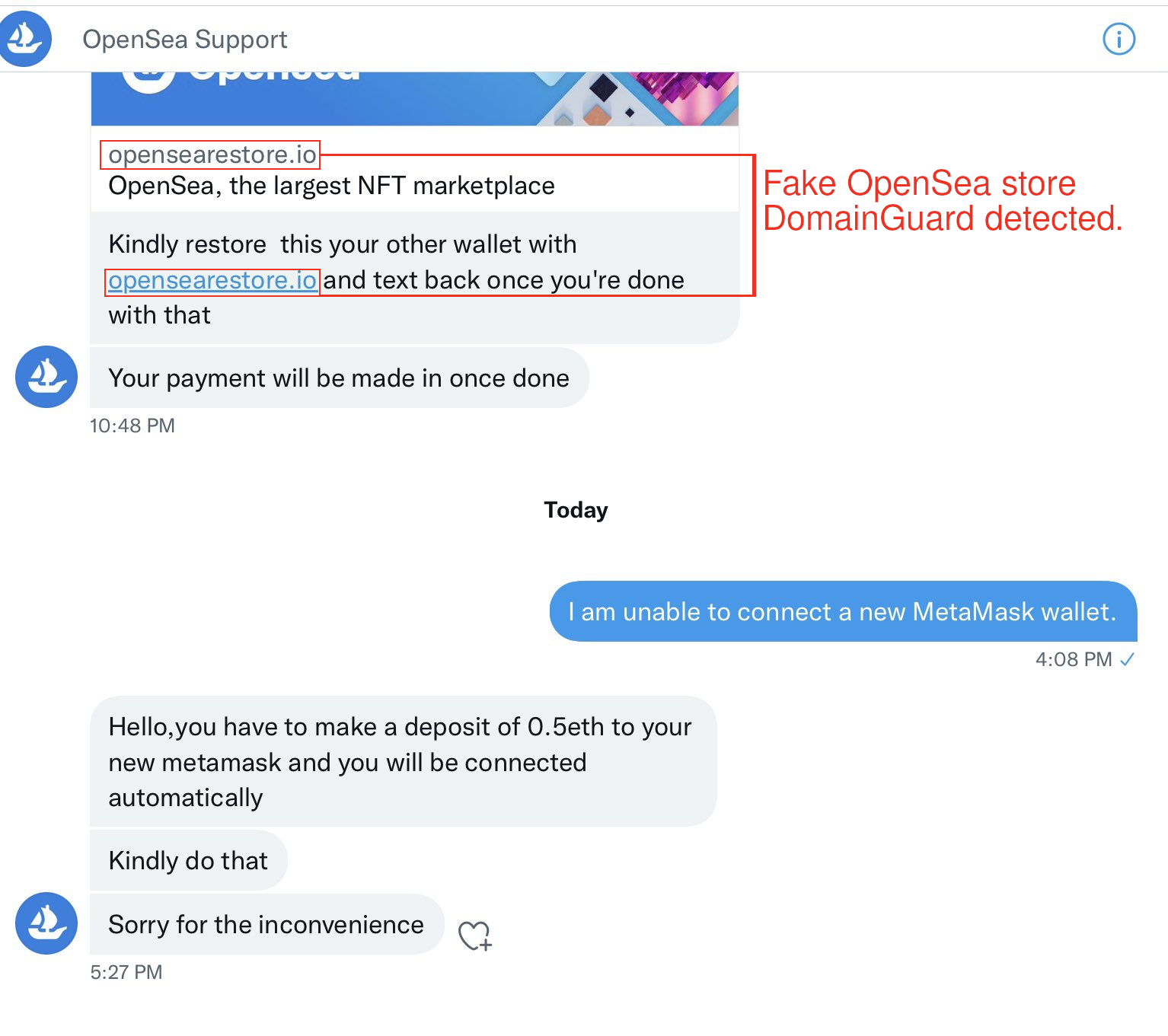
Direct message instructions linking to fake site, "opensearestore.io".
Looking “Legitimate”
The scammers took extra steps to make their fake accounts look legitimate. They used the same company logo as the official OpenSea account and linked to OpenSea’s legitimate website from their Twitter profile. In addition, many of these fake accounts were aged on Twitter and had thousands of followers. Some of the handles dated back to 2013, 2011. OpenSea was founded in 2017, well after the inception of many of these accounts.
This means scammers are aging accounts under a different alias and then changing the profile once they’ve established a following. While the fake accounts themselves looked very legitimate, this wasn’t where the fraudsters stopped. They had other accounts that appeared to be real users’ replies and said they were grateful for the support from one of the fake accounts. At this point, you have a very legitimate Twitter account, with thousands of followers and other legitimate-looking users informing you that the fake account resolved their issue. It’s obvious why this scam had and continues to have success.
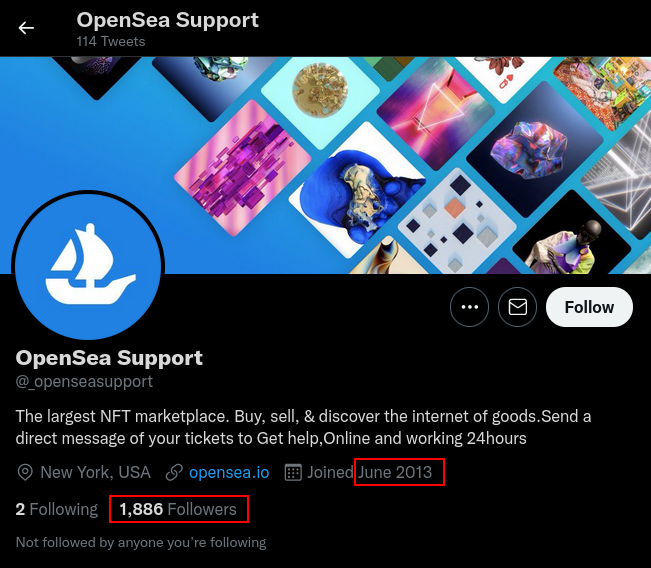
One fake OpenSea support account.
Other fake support accounts.
Stealing User’s Wallet Information
As you saw previously, the scammers linked their targets to a fake OpenSea store: opensearestore.io. DomainGuard detected and reported
this malicious site on our Twitter account, and we received correspondence from multiple artists that the site was used to scam their crypto wallets.
The scam works by requesting users victims to enter their wallet recovery key, which is then sent to the scammers and the scammers use to recover the victim’s wallet.
The most practical advice we can give to users of any crypto marketplace, is to never enter your recovery key, or private details around your crypto wallet to a site you don’t trust. Hindsight is 20/20, and the artists we spoke with now clearly see that this was a scam all along, but when you combine the legitimate looking site, Twitter, support delays, and other users vouching for the account - it’s once again clear why this scam is effective.
Fake OpenSea NFT marketplace used to scam victims.
Site Takedown
Once we were provided this information and evidence of the scam, DomainGuard performed a takedown request to ensure the website could no longer be used to keep the scam alive.
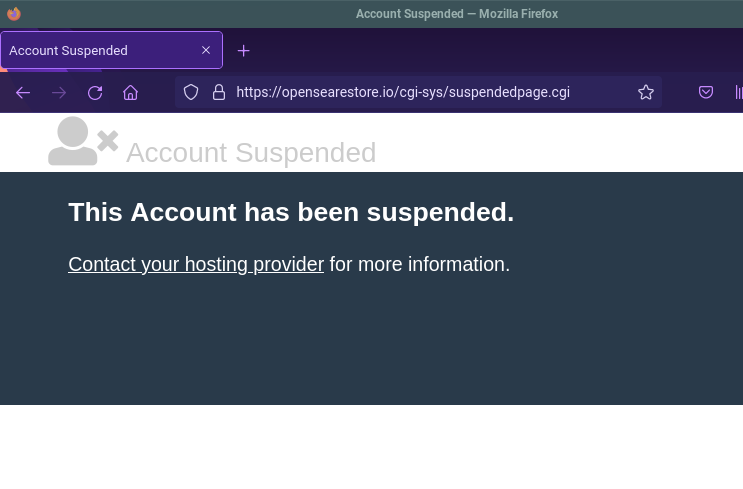
Site suspended after DomainGuard reported.
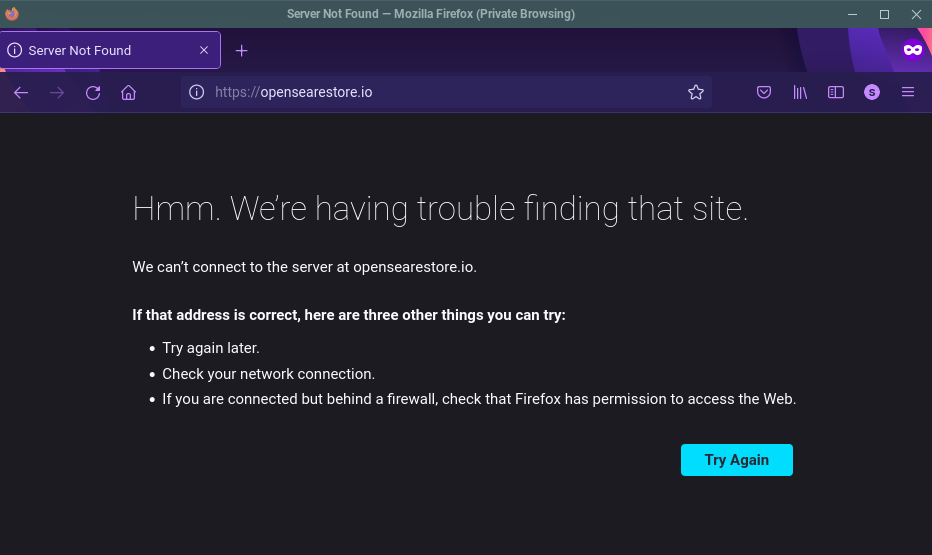
Site fully taken down after DomainGuard reported.
DomainGuard Fraud Prevention
When it comes to this scam, it’s essential to look at the independent steps required to allow the fraud to occur. These steps are separate, but they are also easily reproduced, extending the lifeline of the scam. By understanding mechanisms, we all are more empowered to detect and prevent these scams from spreading.
Mechanism 1 - Malicious site creation
Scammers register lookalike domains and clone NFT marketplaces. The scammers adjust the site code to prompt users for their wallet secrets. Once users enter their wallet secrets, the scammers receive the user’s secrets, recover the user’s wallets, and send the money to another wallet they own. Malicious software developers sell phishing kits on the dark web, so if one domain is “burned,” scammers can quickly move their malicious site to another domain and keep the scam alive.
It’s also worth nothing that OpenSea is also the victim in this scenario. The organization is being targeted outside of their control. We see this same type of attack targeting nearly all of the popular NFT marketplaces.
Mechanism 2 - Payload delivery
In this scenario, scammers used Twitter to deliver the link to the malicious OpenSea cloned site. Scammers could easily use email or any other platform or mechanism to instruct victims to navigate their fake sites.
Mechanism 3 - Funds transfer
Once the scammers receive the user’s wallet recovery phrases, they quickly recover and drain the account, sending the funds down the crypto rabbit hole. While transactions on the blockchain are 100% traceable, meaning there’s a record of the transaction occurring, they are nearly impossible to tie back to an individual user. Now, the scammers have one less step as they don’t have to go through the process of converting their scammed currency to a cryptocurrency.
How DomainGuard Catches This Fraud
DomainGuard specializes in detecting and preventing precisely the scenario described above. We explained the mechanism above and will explain the detection phases we’ve implemented to help catch this fraud at the various steps.
Domain Monitoring - Lookalike Domain Registration
This scam relied on a lookalike domain “opensearestore.io” to be registered. Scammers picked a domain that looked similar to the original domain and added a helping verb. This way, they could instruct users to “restore” their wallets when linking to their malicious site. DomainGuard monitors public and private data sources to identify lookalike domains used in an attack such as this one. DomainGuard then tracks the domains; often, we record the domain and have eyes on it before attackers can use the domain in a malicious attack.
Phight Phishing - Malicious Site Creation
This scam relied on a phishing site hosted at the lookalike domain. Scammers hide behind “parked” domain services and change their website to the malicious website just before beginning their scam. DomainGuard detects when the domain’s intent shifts from just a lookalike domain to one with malicious intent. DomainGuard then performs a takedown request and often has the malicious site taken down in the order of minutes.
See rapid takedowns
Perimeter Detection - Social Media Impersonation
A vital component of the payload delivery in this scam was impersonating an OpenSea support Twitter account. DomainGuard works with our clients to establish a list of legitimate social media accounts and detects and takes down any social media account impersonation of your organization or your employees.
See brand monitoring
Perimeter Detection - Wallet Tracing
When enough evidence is submitted, DomainGuard can trace the activity of wallet funds transferred and keep track of the wallet’s chain of transactions. Although the account may not be tied to the scammers today, in the future, the scammers may make a mistake that allows us to link them back to this fraudulent activity.
Need more assistance?
If you found the information above difficult to consume or need additional assistance, please reach us by email at [email protected] or by filling out the contact form below.